Search for "林水成董事長股份tVwo" returned 1557 results

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
47 min
Jailbreaking iOS
From past to present

55 min
Attribution revolution
Turning copyright upside-down with metadata

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

29 min
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

46 min
CounterStrike
Lawful Interception
38 min
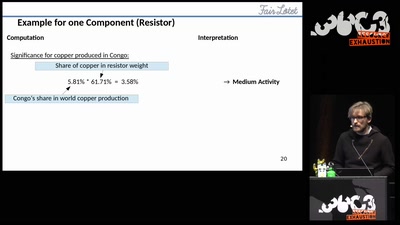
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.
46 min
What The Fax?!
Hacking your network likes it's 1980 again

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

54 min


![Why we are addicted to lithium [1/2]](https://static.media.ccc.de/media/events/rc3/2021/193-3fd1b8af-9ab6-54c5-88ad-2622c1cc925a.jpg)