Search for "453" returned 2032 results

59 min
Security of the IC Backside
The future of IC analysis
61 min
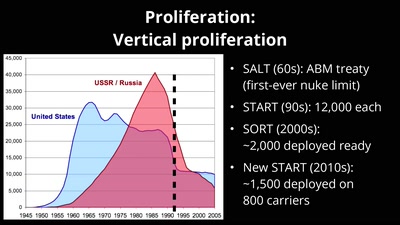
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
47 min
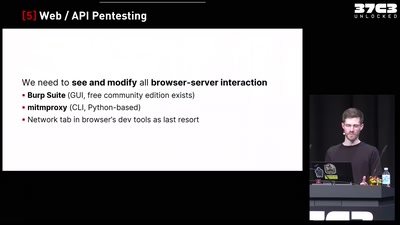
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
56 min
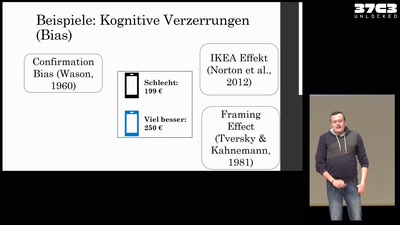
Social Engineering: Geschichte, Wirkung & Maßnahmen.
Alles, was ihr immer über Social Engineering wissen…
61 min
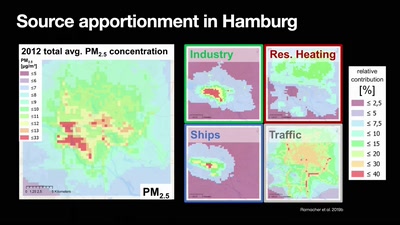
Numerical Air Quality Modeling Systems
a journey from emissions to exposure
43 min
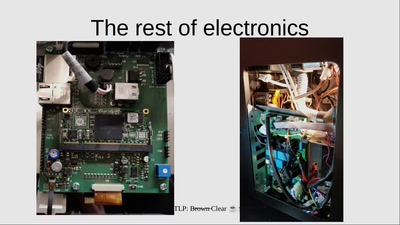
unexpected coffee
a dive into industrial coffee machines
21 min
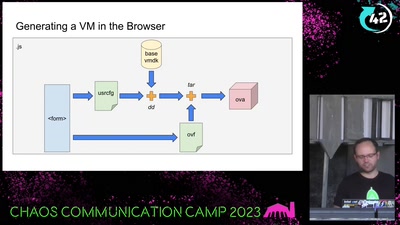
Bootloader Crimes
Building disposable Windows VMs
18 min
c3 MorningShow
Tag 5

50 min
Heimlich-Manöver
Best of Informationsfreiheit & Gefangenenbefreiung

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

41 min
Euclid – das neue Weltraumteleskop
Mit Milliarden leuchtenden Galaxien den dunklen Teil des…
60 min
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…

43 min
Tractors, Rockets and the Internet in Belarus
How belarusian authoritarian regime is using technologies…
115 min