Search for "264" returned 2185 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

70 min
Security Nightmares 0x14
Was Sie schon immer nicht über darüber wissen wollten wer…

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

60 min
Ein Abgrund von Landesverrat
Wie es dazu kam und was daraus zu lernen ist

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

58 min
Switches Get Stitches
Industrial System Ownership

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
40 min
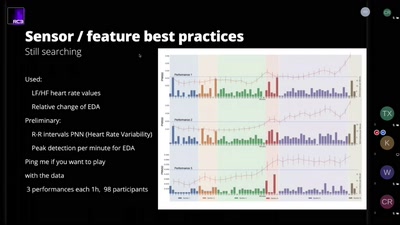
Boiling Mind
Analysing the link between audience physiology and…
38 min
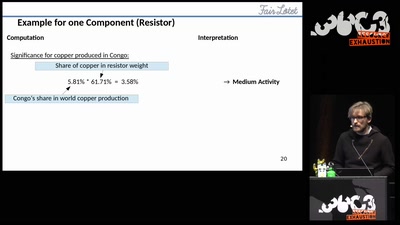
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices
35 min
Wallet Security
How (not) to protect private keys
39 min
Transmission Control Protocol
TCP/IP basics
35 min
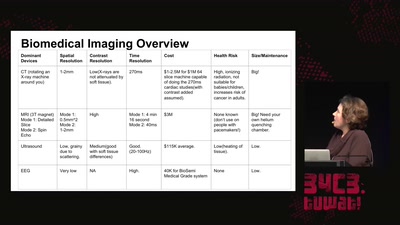
Low Cost Non-Invasive Biomedical Imaging
An Open Electrical Impedance Tomography Project

31 min