Search for "374" returned 1973 results

50 min
Heimlich-Manöver
Best of Informationsfreiheit & Gefangenenbefreiung
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
55 min
YOU’VE JUST BEEN FUCKED BY PSYOPS
UFOS, MAGIC, MIND CONTROL, ELECTRONIC WARFARE, AI, AND THE…
56 min
Social Engineering: Geschichte, Wirkung & Maßnahmen.
Alles, was ihr immer über Social Engineering wissen…
61 min
Numerical Air Quality Modeling Systems
a journey from emissions to exposure

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

32 min
History and implications of DRM
From tractors to Web standards
31 min
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…
61 min
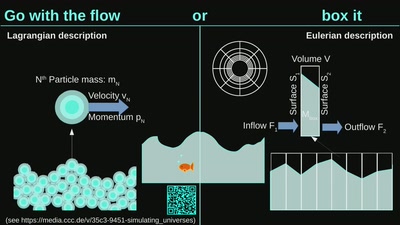
Grow your own planet
How simulations help us understand the Universe

50 min