Search for "578" returned 1911 results

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…
60 min
System Change mit Instagram??
Social Media und die Zivilgesellschaft

62 min
Kyber and Post-Quantum Crypto
How does it work?

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

62 min
To Protect And Infect, Part 2
The militarization of the Internet
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…
59 min
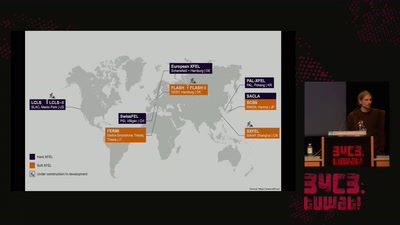
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

41 min