Search for "fake" returned 2878 results

28 min
Making the LSM available to containers
stacking and namespacing the LSM

51 min
Anonymous, secure and easy. You can have them all.
An authentication protocol that offers security, privacy…

50 min
Open Source Your Career
Fast-track your professional development with community…
41 min
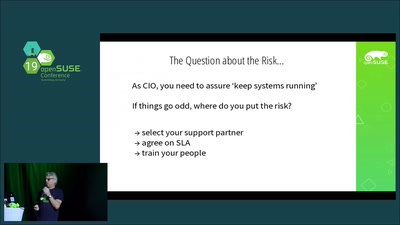
Business Applications as Free Software - Demystifying FUD
You should not believe everything that Big Money tells…

59 min