Search for "fake" returned 2878 results

25 min
Jazda: Rust on my bike
A FLOSS bike computer with Rust

51 min
The ultimate Galaksija talk
Everything about a Yugoslavian microcomputer halfway…
64 min
The Cell Processor
Computing of Tomorrow or Yesterday

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

51 min
Talking people into creating patches
... and submitting them ...

53 min
A Case Against C++
Why C++ is bad for the environment, causes global warming…

19 min
Fooled by the Website Carbon Calculator
Green Coding & Measuring the Environmental Impacts of IT
51 min
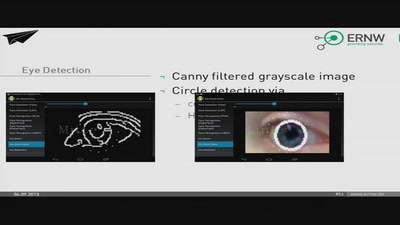
Slide To Unlock -- or Provide Your Facebook Pictures?
A Critical Analysis of Biometric Authentication Mechanisms

109 min
Lightning Talks Day 4
Lightning Talks
122 min
Lightning Talks Day 3
Lightning Talks
47 min