Search for "918" returned 2160 results

45 min
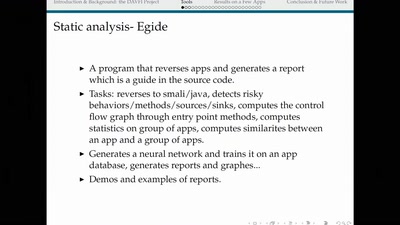
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

43 min
Tractors, Rockets and the Internet in Belarus
How belarusian authoritarian regime is using technologies…

32 min
Cadus e.V.
Chaos Family

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

51 min
Digital Identity and Digital Euro
what is the EU up to now?

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…

47 min
Digitalcourage und die Post DHL Group
eine Chronik
46 min
Public Money bei der Arbeit
die Deutsche Verwaltung und Open Source
59 min
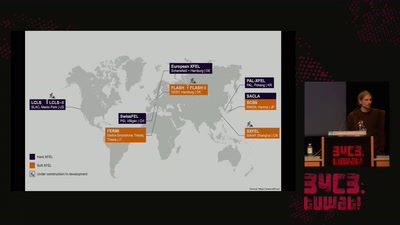
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.
43 min