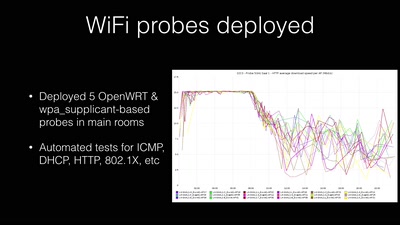
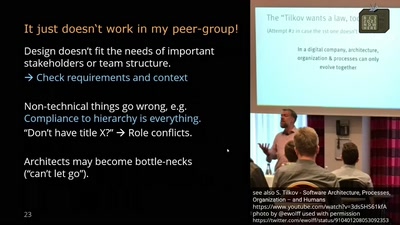
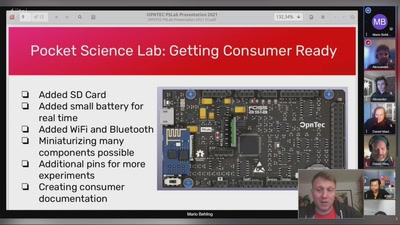
Search for "FOSS" returned 602 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
60 min
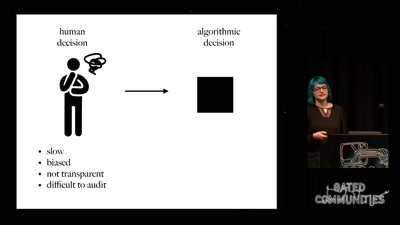
Prediction and Control
Watching Algorithms

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

62 min
Deine Rechte sind in diesen Freihandelsabkommen nicht verfügbar
Der Protest gegen TTIP und CETA

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

55 min
The DROWN Attack
Breaking TLS using SSLv2

60 min
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…

56 min
WarGames in memory
what is the winning move?

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

58 min