Search for "841" returned 1866 results
31 min
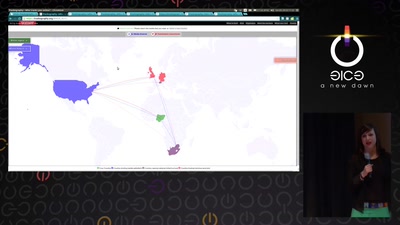
Trackography
You never read alone

46 min
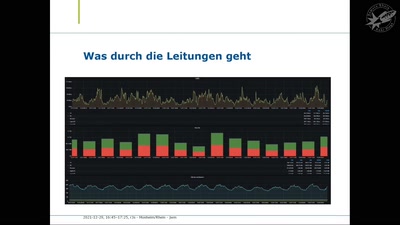
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

46 min
CounterStrike
Lawful Interception

54 min
A la recherche de l'information perdue
some technofeminist reflections on Wikileaks

60 min
Why is GPG "damn near unusable"?
An overview of usable security research
40 min
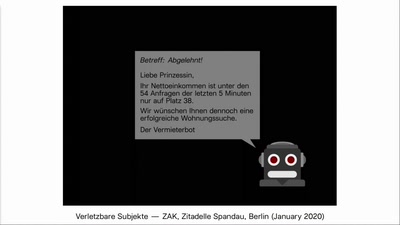
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution
35 min
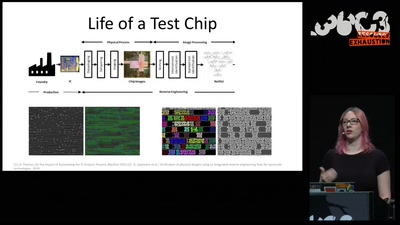
Understanding millions of gates
Introduction to IC reverse engineering for…
62 min
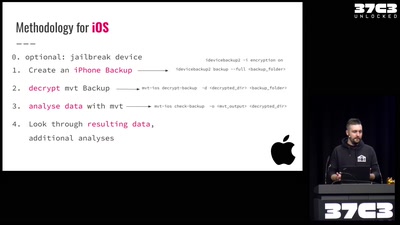
Einführung in Smartphone Malware Forensik
Wie man Stalkerware und Staatstrojaner auf Smartphones…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

51 min