Search for "Tom Wills" returned 4691 results
24 min
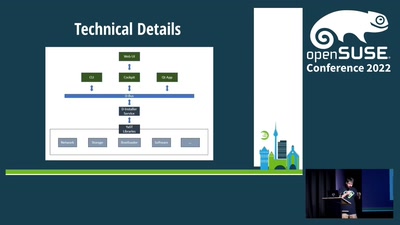
D-Installer Project: Carving a Modern Installer
A new installer based on D-Bus, YaST, Cockpit and web…

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

44 min
Hackerfleet - what happend?
Discussion round
38 min
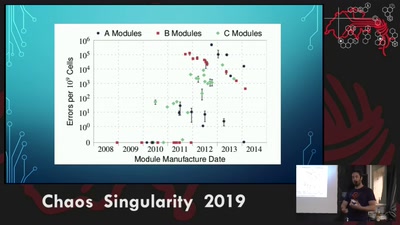
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used
40 min