Search for "Luca" returned 342 results

58 min
Baseband Exploitation in 2013
Hexagon challenges

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…
58 min
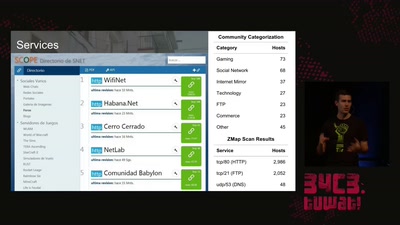
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…

58 min
Virtual Machine Introspection
From the Outside Looking In

61 min
Vacuum robot security and privacy
prevent your robot from sucking your data

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

72 min
Console Hacking
Breaking the 3DS

58 min
Überwachen und Sprache
How to do things with words

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…
53 min
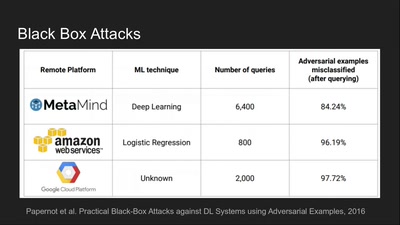
Deep Learning Blindspots
Tools for Fooling the "Black Box"
64 min
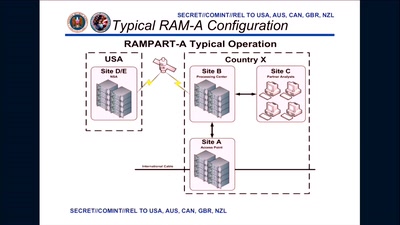
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
48 min
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

147 min