Search for "Thde" returned 8451 results
45 min
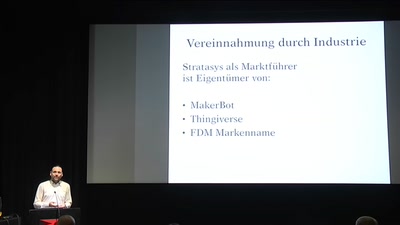
FabLabs are not Hackerspaces!
The story of an art driven 3D printing research facility

31 min
openSUSE ALP prototype on AWS, experimental, but fun!
Experiences, challenges and how SUSE NeuVector came into…

32 min
DNF vs ZYpp: Fight!
A comparison of the two major RPM package managers

25 min
Regulating Autonomous Weapons
The time travelling android isn’t even our biggest problem

33 min
Social cooling
How the reputation economy is turning us into conformists

30 min
NexMon - Make Wi-Fi hacking on smartphones great again!
Reverse engineering of the Nexus 5 Wi-Fi chip

66 min
Podjournalism
The Role of Podcasting in Critical and Investigative…

82 min
Attacking NFC mobile phones
First look at the security of NFC mobile phones
38 min
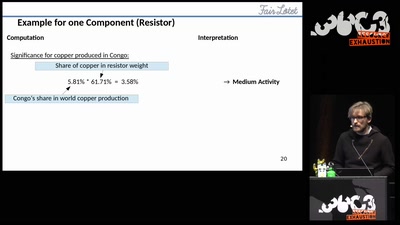
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices
32 min
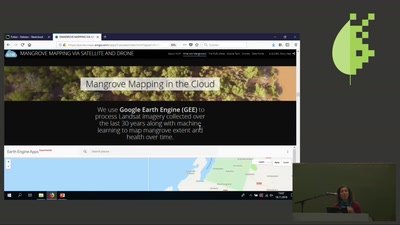
Mangrove Conservation via Satellite
using the latest technology to map and monitor mangroves

27 min
Heroes, not Superheroes
What the Heroes would prefer not to tell you ;-)
48 min
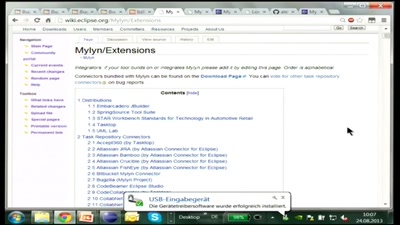
Fokussiertes Arbeiten mit Mylyn
Effectively use the integrated Task-focused UI in Eclipse
44 min
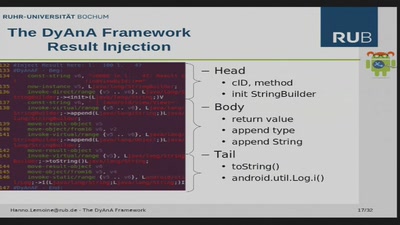
Dynamic Malware Analysis on Android Phones
Presentation of the DyAnA Framework (Dynamic Android…

63 min
Print Me If You Dare
Firmware Modification Attacks and the Rise of Printer…
38 min
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used

40 min
LibreRouter demo
Lessons learned developing open source hardware for the…
44 min
Legacy Crypto Never Dies
Cracking DES nearly 20 years after the EFF DES Cracker

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

49 min
This is why you can’t make nice stuff
… or the joy of disposing of 5 tons of refrigerators

48 min
Oil Into Digits
A short exploration of the relation between energy and…

68 min
"Spoilers, Reverse Green, DECEL!" or "What's it doing now?"
Thoughts on the Automation and its Human interfaces on…

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…
45 min
Implementation of MITM Attack on HDCP-Secured Links
A non-copyright circumventing application of the HDCP…

56 min
Blackbox JTAG Reverse Engineering
Discovering what the hardware architects try to hide from…
61 min