Search for "Thde" returned 8451 results
54 min
Infrastructure review
How all the infra teams made SHA2017 possible

20 min
Next Generation Storage for YaST
Why Users should look forward to the Redesign.

61 min
Cross distribution packaging
Using the openSUSE BuildService for coss distribution…

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

59 min
SmartMeter
A technological overview of the German roll-out
55 min
All your base(s) are belong to us
Dawn of the high-throughput DNA sequencing era

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society
42 min
Making a Wordclock
using Python to show the time in style
17 min
"Information. What are they looking at?"
A documentary on privacy for the broad audience.

49 min
Lawful Interception in VoIP networks
Old Laws and New Technology the German Way
60 min
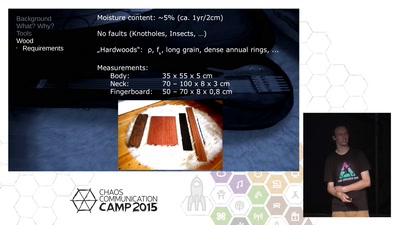
A Hackers Approach To Building Electric Guitars
Let's do everything except the pots by ourselves
60 min
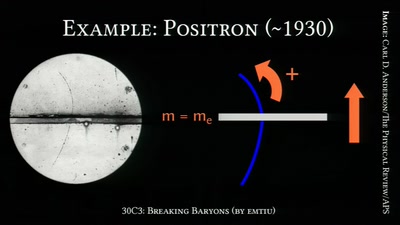
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders

34 min
Playstation Portable Cracking
How In The End We Got It All!

58 min
Counterlobbying EU institutions
How to attempt to counter the influence of industry…
35 min
Remote Attestation in MicroOS
Measuring the health of our system with a TPM

41 min
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…
25 min
Uyuni: introduction, last year's updates and future
What is Uyuni? - What's been going on the last year? -…
41 min
Introduction to (home) network security.
A beginner-friendly guide to network segmentation for…
60 min
Ghidra - An Open Source Reverse Engineering Tool
How the NSA open-sourced all software in 2019
47 min
Distributed Actor System with Rust
Learn about the building blocks of a network application
42 min
Terminator Genes and GURT - Biological Restrictions Management
Five Years after the announcement of a quasi moratorium

52 min
Adventures in Mapping Afghanistan Elections
The story of 3 Ushahidi mapping and reporting projects.

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

53 min