Search for person "Angela Mueller" returned 25 results
40 min
Unlocked! Recovering files taken hostage by ransomware
Decrypting files hijacked by the "second most used…

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…

57 min
Towards a more secure operating system without sacrificing usability
aka the GNOME challenge:

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

136 min
CyberMorning Show
Cyber Gulasch
54 min
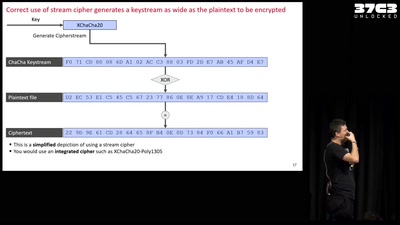
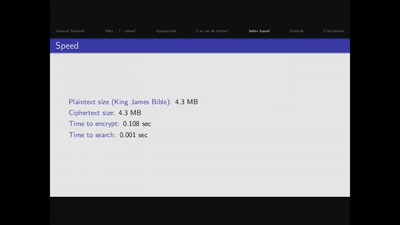
The World of Searchable Encryption
A glimpse into advanced cryptogrpahic schemes
45 min
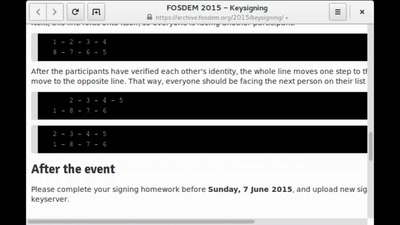
Two decades later - Keysigning in the 2000s
Micro keysigning parties for the masses

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

73 min
What's cooking in GNOME?
GNOME 3.12 - Design Decisions, Main Changes, Future Visions
49 min
Eliminating DOM-based XSS
Or: How taint tracking in Chromium works
30 min