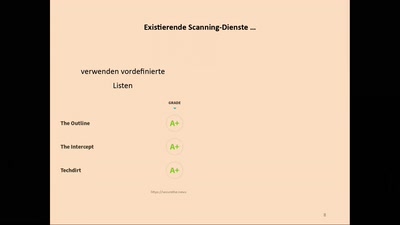
Search for person "Andy Mueller-Maguhn" returned 59 results
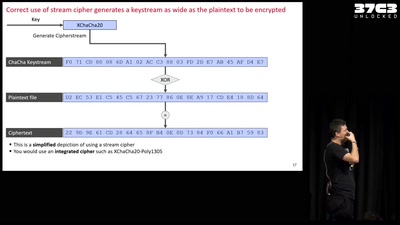
40 min
Unlocked! Recovering files taken hostage by ransomware
Decrypting files hijacked by the "second most used…

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

57 min