Search for "10" returned 5090 results

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
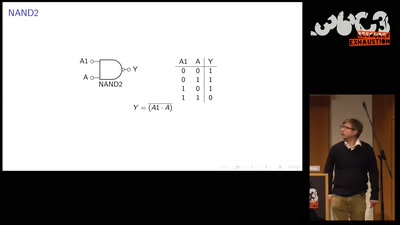
60 min
LibreSilicon's Standard Cell Library (de)
show + tell
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

60 min
Von Kaffeeriechern, Abtrittanbietern und Fischbeinreißern
Berufe aus vergangenen Zeiten
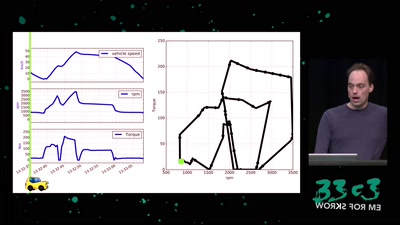
60 min
Software Defined Emissions
A hacker’s review of Dieselgate

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
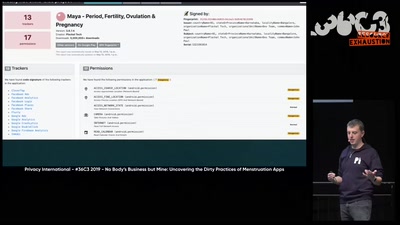
52 min
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…

46 min
CounterStrike
Lawful Interception
64 min
Hacking the Media: Geflüchtete schmuggeln, Nazis torten, Pässe fälschen
Warum wir zivilen Ungehorsam und Subversion mehr brauchen…

30 min