Search for "51" returned 3726 results

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

27 min
Italy's surveillance toolbox
Research on Monitoring Italian Government Surveillance…

50 min
Connected Mobility hacken: digital.bike.23
Von E-Bikes in der Connected Mobility zur Entstehung eines…

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming
37 min
Listening Back Browser Add-On Tranlates Cookies Into Sound
The Sound of Surveillance

30 min
0en & 1en auf dem Acker
Was die Sensor & Automatisierungstechnik in der…

29 min
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...

29 min
Es sind die kleinen Dinge im Leben II
was alles geht und wie man anfängt, mit Mikroskopen

38 min
The Planet Friendly Web
Warum unser Web nachhaltiger werden muss und wie wir das…

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

55 min
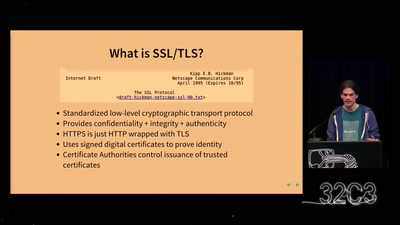
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

31 min
TrustZone is not enough
Hijacking debug components for embedded security

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

33 min
Global Civil Society Under Attack
Reports from the Frontlines
31 min
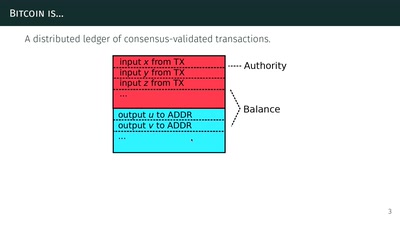
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…
28 min