Search for "26" returned 4319 results

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…
66 min
31C3 Keynote
A New Dawn

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
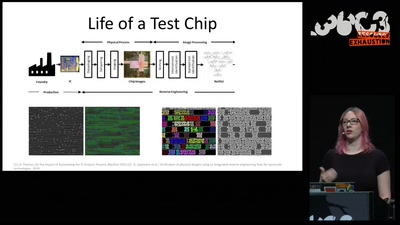
35 min
Understanding millions of gates
Introduction to IC reverse engineering for…

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

70 min
Security Nightmares 0x14
Was Sie schon immer nicht über darüber wissen wollten wer…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…
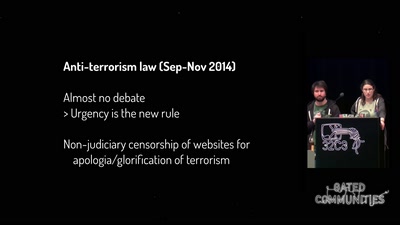
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

58 min
Switches Get Stitches
Industrial System Ownership

26 min
Technomonopolies
How technology is used to subvert and circumvent…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

43 min