Search for "15" returned 4930 results

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…
42 min
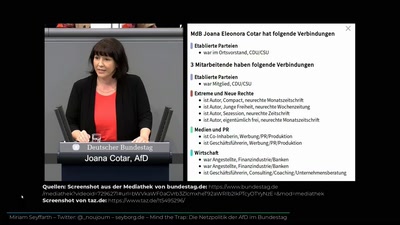
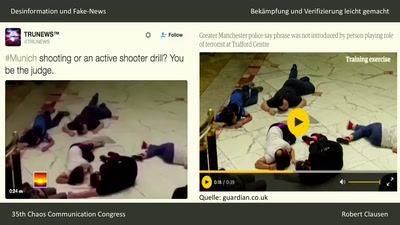
Desinformation und Fake News
Bekämpfung und Verifizierung leicht gemacht

72 min
Console Hacking
Breaking the 3DS

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

44 min
Fallstricke der Anonymisierung
Auf unserer Onlineplattform können Studierende…

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
40 min
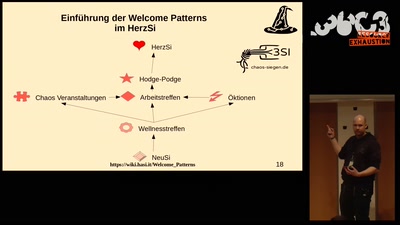
Welcome Pattern - Theorie und Praxis
(Eine Gemeinschaftsproduktion der Haecksen, der…

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…

58 min
PLC-Blaster
Ein Computerwurm für PLCs
56 min
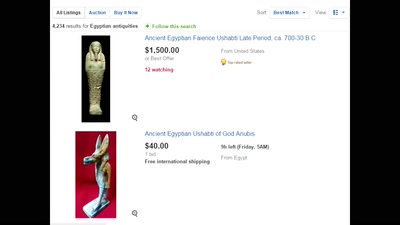
The mummy unwrapped
Cultural Commons durch Kunstraub

60 min