Search for "41" returned 3836 results
35 min
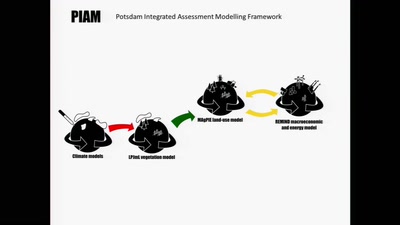
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

33 min
Beyond Virtual and Augmented Reality
From Superhuman Sports to Amplifying Human Senses

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

60 min
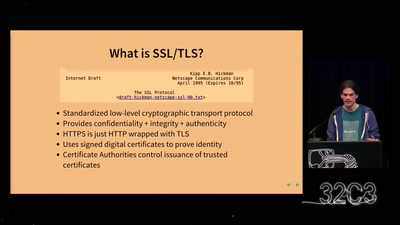
Why is GPG "damn near unusable"?
An overview of usable security research
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

62 min
Deine Rechte sind in diesen Freihandelsabkommen nicht verfügbar
Der Protest gegen TTIP und CETA
61 min
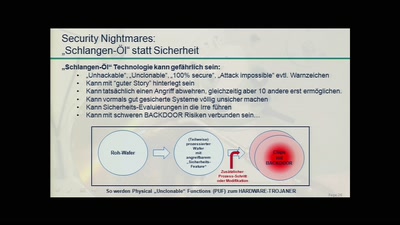
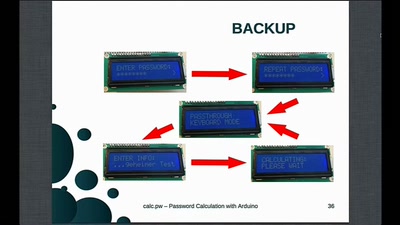
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

61 min




![Why we are addicted to lithium [1/2]](https://static.media.ccc.de/media/events/rc3/2021/193-3fd1b8af-9ab6-54c5-88ad-2622c1cc925a.jpg)