Search for "39" returned 3516 results

58 min
When hardware must „just work“
An inside look at x86 CPU design

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

55 min
White-Box Cryptography
Survey
31 min
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data
62 min
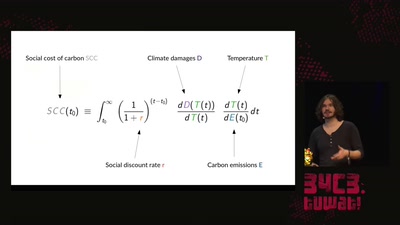
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14
31 min
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…
31 min
DPRK Consumer Technology
Facts to fight lore

58 min