Search for "27" returned 4139 results

60 min
Vor Windows 8 wird gewarnt
Und nichts (Secure) Bootet mehr?
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…

61 min
Die göttliche Informatik
Die Informatik löst formale (mathematisch modellierte)…

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
46 min
The Mission of the MV Louise Michel
"Feminism will be anti-racist or it won´t be"

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
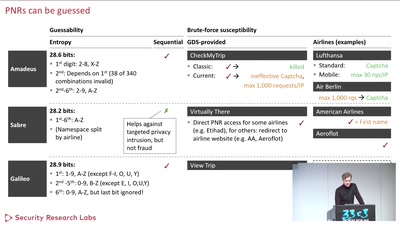
59 min
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

30 min
0en & 1en auf dem Acker
Was die Sensor & Automatisierungstechnik in der…
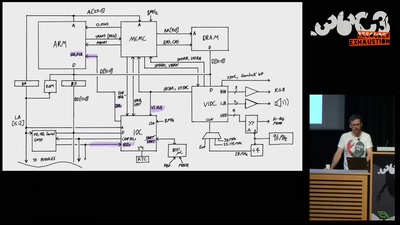
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
apertus° AXIOM
The first Open Source Cinema Camera

31 min
BGP and the Rule of Custom
How the internet self-governs without international law

33 min