Search for "33" returned 3656 results

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice
30 min
“Nabovarme” opensource heating infrastructure in Christiania
Freetown Christiania´s digitally controlled/surveyed…

40 min
Radical Digital Painting
Fantastic Media Manipulation

63 min
goto fail;
exploring two decades of transport layer insecurity
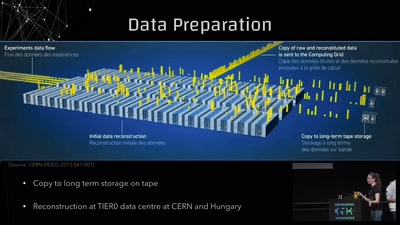
41 min
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

57 min