Search for "14" returned 4701 results

53 min
From Maxwell to antenna arrays
How 150 year old equations still help to communicate

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…
60 min
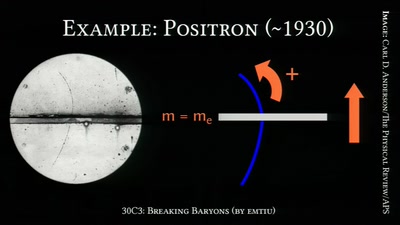
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

51 min
Funky File Formats
Advanced binary tricks

43 min
How Facebook tracks you on Android
(even if you don’t have a Facebook account)

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
36 min



![Resistance against dictatorship in Belarus in times of war [EN]](https://static.media.ccc.de/media/events/datenspuren/2024/463-72bfad55-bbd5-5dad-9a8f-9109ed64b787.jpg)