Search for "30" returned 4239 results

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

59 min
Zwischen supersicherer Verschlüsselung und Klartext liegt nur ein falsches Bit
Ein Streifzug durch die Fehler in der Kryptografie

34 min
Ling - High level system programming
modular and precise resource management

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

62 min
Let's Encrypt
A Free Robotic Certificate Authority

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics
62 min
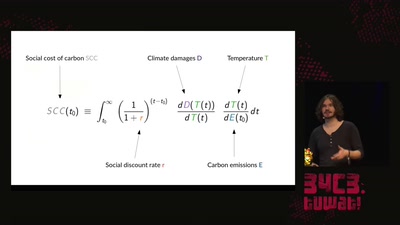
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

40 min