Search for "10" returned 5075 results
61 min
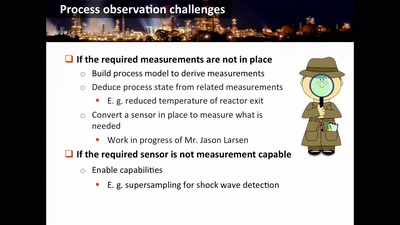
Damn Vulnerable Chemical Process
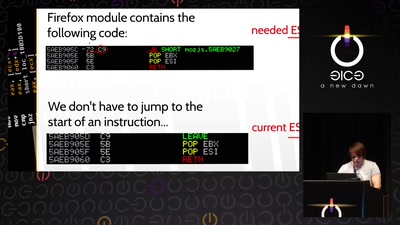
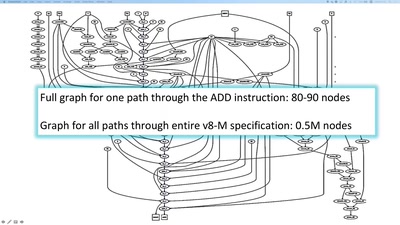
Exploitation in a new media

55 min
Attribution revolution
Turning copyright upside-down with metadata

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

51 min
The GNU Name System
A Decentralized PKI For Social Movements

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

34 min
Haft für Whistleblower?
Demokratiefeindliches Strafrecht: Die Datenhehlerei gem. §…
55 min
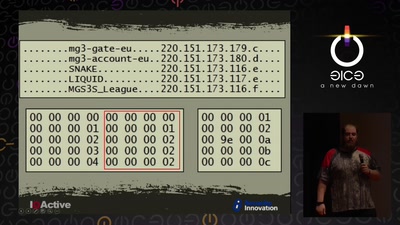
Cyber Necromancy
Reverse Engineering Dead Protocols

34 min