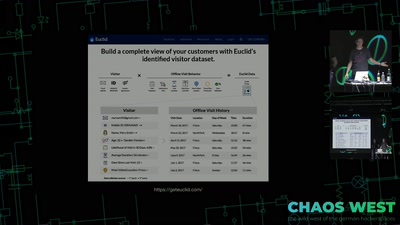
Search for "10" returned 5081 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

61 min
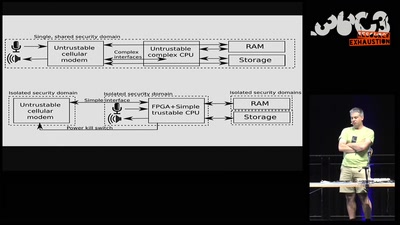
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

58 min
Virtual Machine Introspection
From the Outside Looking In
49 min
Creating Resilient and Sustainable Mobile Phones
Be prepared for the coming Digital Winter. And play…

42 min
A world without blockchain
How (inter)national money transfers works

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…

61 min
Die göttliche Informatik
Die Informatik löst formale (mathematisch modellierte)…
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…
59 min