Search for "13" returned 4825 results
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!

65 min
Mind-Hacking mit Psychedelika
Eine Einführung in die Wirkungsweise psychedelischer…

29 min
lasers in space
more than just pew pew!
36 min
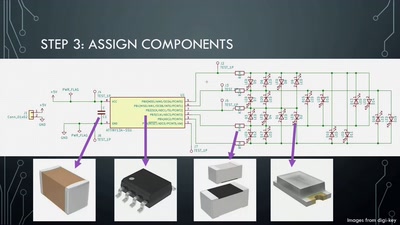
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

41 min
Locked up science
Tearing down paywalls in scholarly communication

60 min
Shopshifting
The potential for payment system abuse

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets
64 min
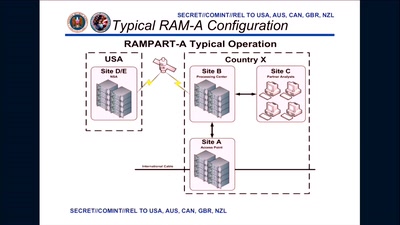
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
55 min
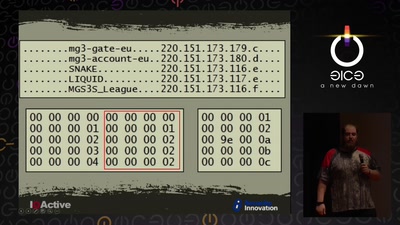
Cyber Necromancy
Reverse Engineering Dead Protocols

57 min
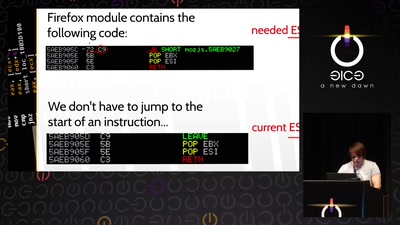
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

60 min
Windows drivers attack surface
some 'new' insights
60 min
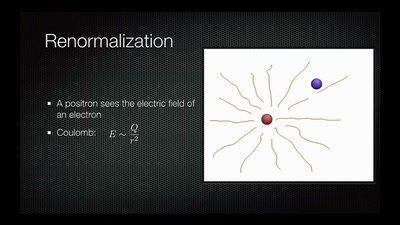
Desperately Seeking Susy
A farewell to a bold proposal?

47 min
![Resistance against dictatorship in Belarus in times of war [EN]](https://static.media.ccc.de/media/events/datenspuren/2024/463-72bfad55-bbd5-5dad-9a8f-9109ed64b787.jpg)