Search for "12" returned 5136 results

60 min
Tiger, Drucker und ein Mahnmal
Neues vom Zentrum für Politische Schönheit

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

61 min
Die göttliche Informatik
Die Informatik löst formale (mathematisch modellierte)…
60 min
Build your own NSA
How private companies leak your personal data into the…

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…
59 min
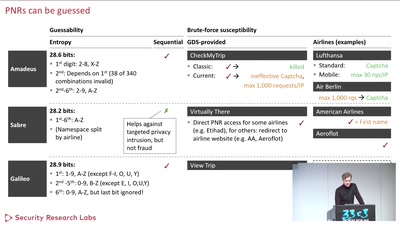
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

54 min