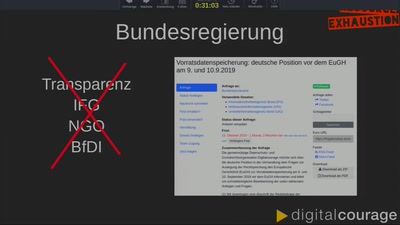
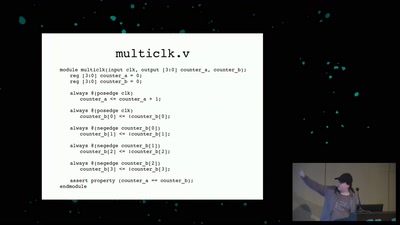
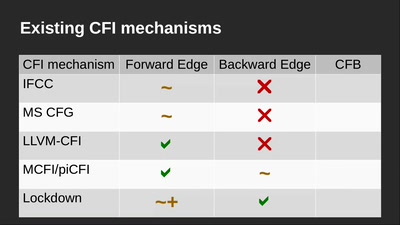
Search for "18" returned 4658 results

60 min
Shopshifting
The potential for payment system abuse

51 min
Funky File Formats
Advanced binary tricks

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

58 min
Open Source Estrogen
From molecular colonization to molecular collaboration

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min
Concepts for global TSCM
getting out of surveillance state mode

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle
61 min