Search for "42" returned 3773 results

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
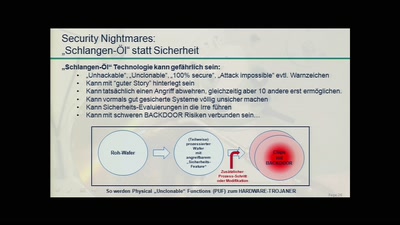
61 min
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft

63 min