60 min
Beyond your cable modem
How not to do DOCSIS networks

60 min
Shopshifting
The potential for payment system abuse

60 min
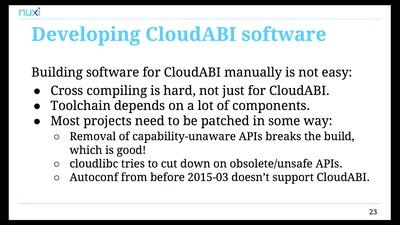
Check your privileges!
How to drop more of your privileges to reduce attack…

29 min
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...

72 min
Console Hacking
Breaking the 3DS

60 min
Hardware-Trojaner in Security-Chips
Eine Reise auf die dunkle Seite

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols
60 min
The Perl Jam 2
The Camel Strikes Back
60 min
Unpatchable
Living with a vulnerable implanted device

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
PLC-Blaster
Ein Computerwurm für PLCs

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
56 min
Running your own 3G/3.5G network
OpenBSC reloaded

60 min
Windows drivers attack surface
some 'new' insights

43 min