Search for "264" returned 2201 results

54 min
World War II Hackers
Stalin's best men, armed with paper and pen
60 min
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
63 min
Das Assange-Auslieferungsverfahren
Als Prozessbeobachter in London

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
58 min
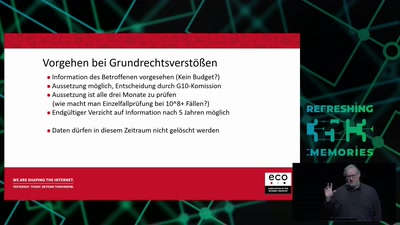
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

63 min
Reconstructing narratives
transparency in the service of justice

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

51 min