Search for ".yof" returned 7511 results
43 min
Hacking Containers and Kubernetes
Exploiting and protecting containers with a few lines of…
38 min
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

48 min
Oil Into Digits
A short exploration of the relation between energy and…

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…
61 min
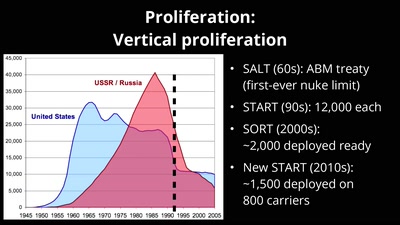
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away
_forget_your_secret_crypto_key.jpg)
34 min
How to (really) forget your secret crypto key
What you always wanted to know about Flash memory - but…

47 min
Organizational Psychology and Software Teams
Measurable Connections between Psychological Constructs and…

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet

56 min
Efficiency & Madness in the Technosphere
Working towards an informed and constructive civil society…
60 min
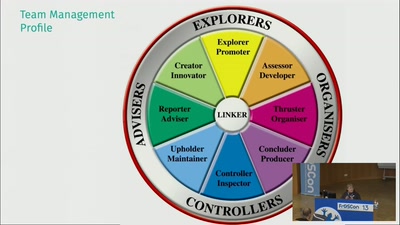
12 years as QA in Agile Teams - what has worked and what hasn't
Tales and experiences with people, ways of working, and…

54 min
Collateral Damage
Consequences of Spam and Virus Filtering for the E-Mail…

55 min
Copyright Enforcement Vs. Freedoms
ACTA, IPRED3 and other upcoming battles of the crusade…
60 min
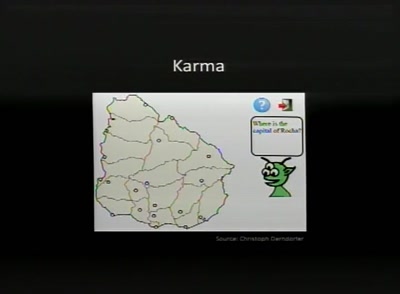
After the Hype
The current state of One Laptop per Child and Sugar Labs

56 min
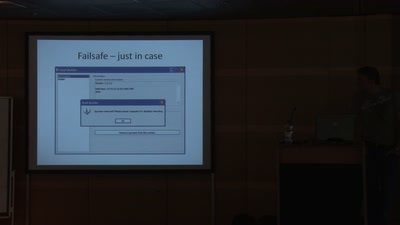
JTAG/Serial/FLASH/PCB Embedded Reverse Engineering Tools and Techniques
a dump of simple tools for embedded analysis at many layers
63 min
Malware Joe Blobs
An overview of stuff that "Malware Joe" puts into his…
57 min