Search for "fake" returned 2878 results
35 min
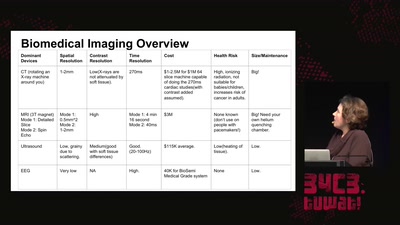
Low Cost Non-Invasive Biomedical Imaging
An Open Electrical Impedance Tomography Project

32 min
Visceral Systems
Approaches to working with sound and network data…

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

64 min
We only have one earth
A case for expansionistic space policy
38 min
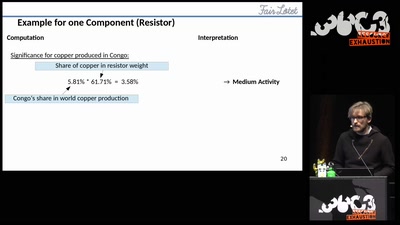
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices
37 min
Music on Mars?
A Musical Adventure for Astronauts and the Space Cadets Who…

30 min
Electroedibles
Open Source Hardware for Smart Candies

36 min
Modchips of the State
Hardware implants in the supply-chain

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…
44 min
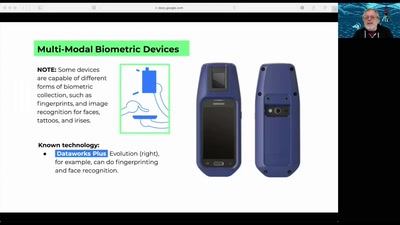
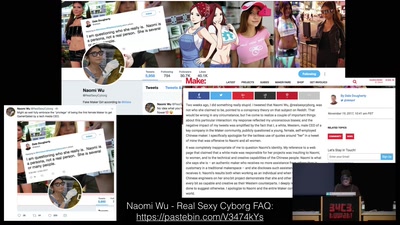
Spot the Surveillance
How to Identify Police Surveillance at Protests and Large…
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…

59 min