Search for "356" returned 2056 results

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

60 min
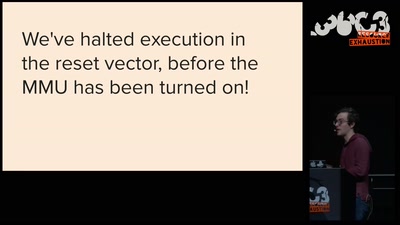
the possibility of an army
phone verified accounts bringing the Hessian army back to…

56 min
WarGames in memory
what is the winning move?

55 min
The DROWN Attack
Breaking TLS using SSLv2

32 min
Die Sprache der Überwacher
Wie in Österreich über Sicherheit und Überwachung…
60 min
Media Coverage and the Public in the Surveillance Society
Findings from a Research Project on Digital Surveillance…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

58 min
Hack_Curio
Decoding The Cultures of Hacking One Video at a Time
72 min
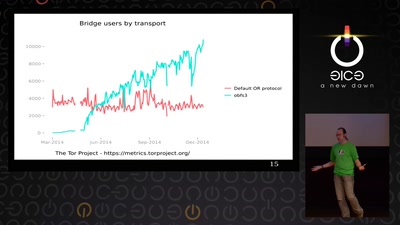
State of the Onion
Neuland

61 min
Uncaging Microchips
Techniques for Chip Preparation

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle
62 min
SuperMUC-NG
… und das Rennen um den schnellsten Computer der Welt
60 min
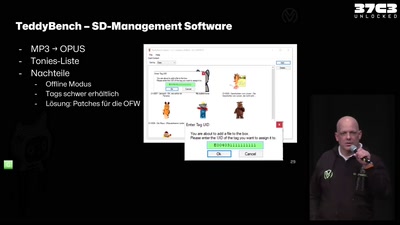
Toniebox Reverse Engineering
Eine Musikbox für Kinder, Maker und Hacker

58 min
Die Krise der Bilder ist die Krise der Politik
Die Krise der Politik ist die Krise der Bilder

58 min
Virtual Machine Introspection
From the Outside Looking In

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist
57 min