Search for "jk" returned 2275 results

33 min
Hacking as Artistic Practice
!Mediengruppe Bitnik about their recent works

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
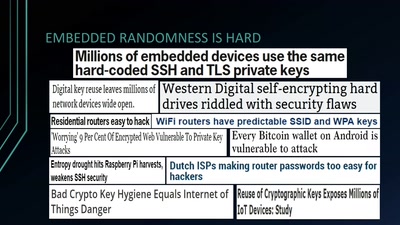
36 min
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

58 min
Virtual Machine Introspection
From the Outside Looking In

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

46 min
Climate Modelling
The Science Behind Climate Reports

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

30 min
The Magical Secrecy Tour
A Bus Trip into the Surveillance Culture of Berlin One Year…

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study
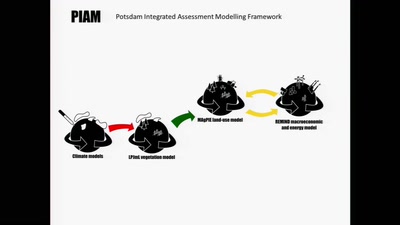
35 min
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy

30 min
Forging the USB armory
Creating an open source secure flash-drive-sized computer
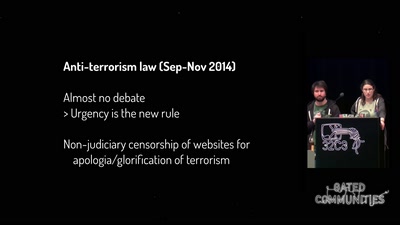
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

46 min