Search for "atd" returned 7638 results
55 min
"How I met your pointer"
Hijacking client software for fuzz and profit
27 min
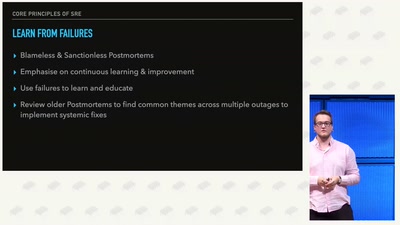
Site Reliability Engineering Explained
An Exploration of DevOps, Platform Engineering, and SRE
41 min
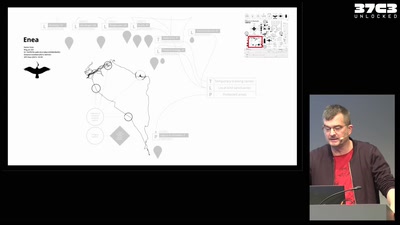
Infrastructure of a migratory bird
Technology and autonomy in more-than-human networks
39 min
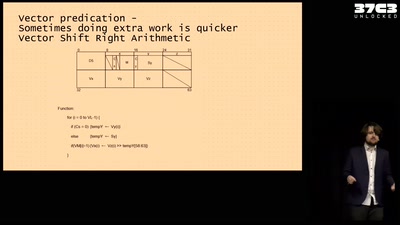
Making homebrew for your very own Vector Super Computer
Adventures running a NEC Vector Engine for fun and ...…

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

38 min
The impact of quantum computers in cybersecurity
Estimating the costs of algorithms for attacks and defense…

53 min
Documentation with any editor
Create beautiful documentation in the editor of your choice…

54 min
Pray to the Omega Point
Religious ideas and techno-futurism. The Rapture for nerds,…

41 min
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…
25 min
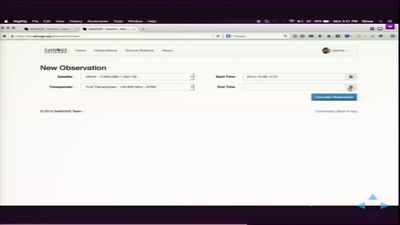
Satellite Open Ground Station Network
open source ground station, optimized for modularity, built…

54 min
Samsung Camera to Mastodon Bridge
Giving old Samsung compact and mirrorless cameras…

44 min
Why This All Matters
A Key Note by Rick Spencer
34 min
Making video games in a weekend
The why and how of game jams
36 min
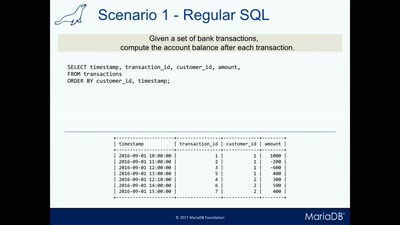
Faster Analytics with MariaDB 10.2
Advanced SQL features - CTEs and Window Function

15 min
YaST: from the repository to the distributions
Continuous testing and delivery, the YaST way

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures

73 min
Conlanging 101
I make languages (and you can too)

68 min
Inside VMware
How VMware, VirtualPC and Parallels actually work

51 min
sva erzaehlt von Indien
hillhacks - hacking and making in the Himalayas
46 min
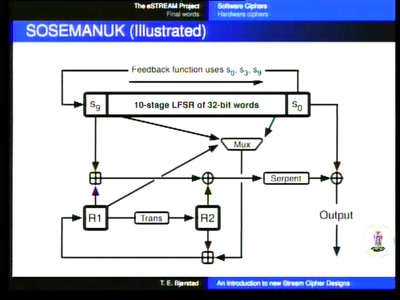
An introduction to new stream cipher designs
Turning data into line noise and back

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
55 min
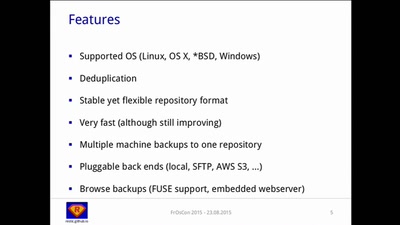
A Solution to the Backup Inconvenience
Fast, Secure and Efficient Backups with "restic"

21 min
Another Approach to AI
An approach to ethical AI focussed on transparency and…
65 min
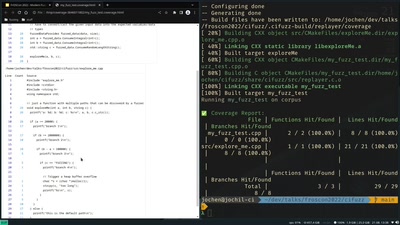
Introduction to modern fuzzing
Find and fix vulnerabilities before they reach production.

14 min