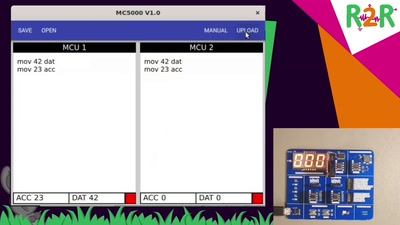
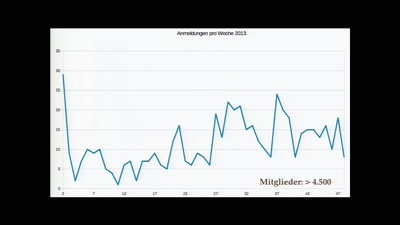
Search for "ilf" returned 2565 results

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…
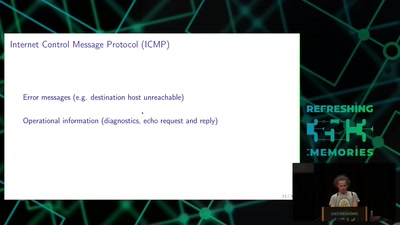
39 min
Transmission Control Protocol
TCP/IP basics
39 min
Gamified Control?
China's Social Credit Systems

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools
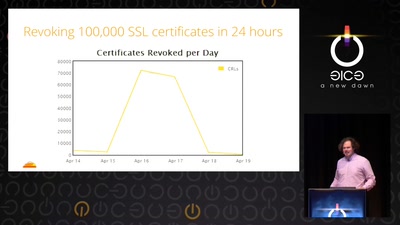
29 min
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!
42 min