Search for ".dol" returned 2663 results

38 min
openSUSE & Jurrassic Park
What should we do about Containerised Applications?

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
28 min
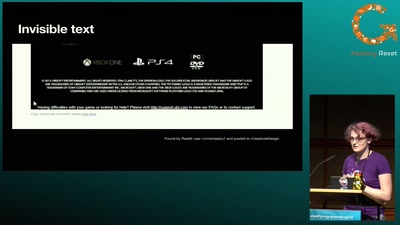
Come to the dark side, they have cookies
How dark patterns manipulate users to do things they don’t…
38 min
Konferenzorganisation mit Ruby
Do-It-Yourself Konferenzmanagement und Videostreaming

58 min
Überwachen und Sprache
How to do things with words

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

53 min
Towards a Single Secure European Cyberspace?
What the European Union wants. What the hackerdom can do..

64 min
Cyberpeace and Datalove
How do we counter the memes of control?

40 min
Crypto Dawn
A To Do list for Cyptographic Research and Implementations

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…
87 min
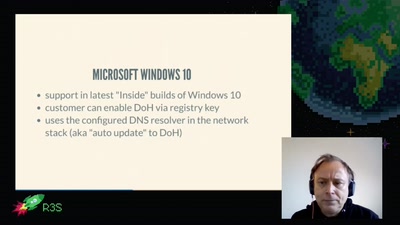
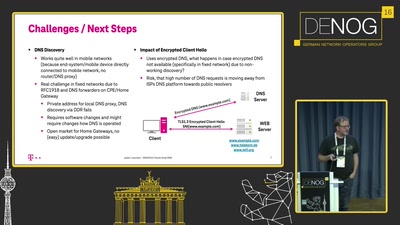
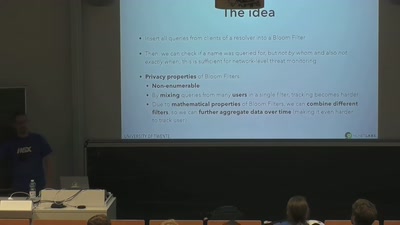
DNS privacy and security
Chaos Colloquium #1

59 min
e-Voting: The silent decline of public control
Why German voting machines do not meet the requirements of…

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…
49 min