Search for "atd" returned 7633 results
69 min
The hills are alive with the sound of hacking ... don't wake the monkeys!
The State of the Hack in India. A place to be^W hack in the…
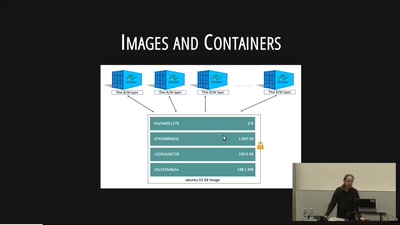
27 min
Dockerize stuff
Postgis swarm and other geo boxes

30 min
Gems are truly outrageous
Combining 3D printing and crystallisation techniques

61 min
FaceDancer 2.0
easy USB hacking, sniffing, and spoofing

101 min
DG73: Hacking with Care
Tactical and ethical care for all

56 min
Space Federation
Linking and Launching Earth-Based Hackerspaces

47 min
String Oriented Programming
Circumventing ASLR, DEP, and Other Guards
47 min
https://netzsin.us - Dem Stromnetz auf die Finger geguckt
Netzfrequenz messen for fun and profit
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine
47 min
Replacing Docker with Podman
Simple tool for running pods and containers
73 min
hacking smart phones
expanding the attack surface and then some

59 min
Literarisches Code-Quartett
The good, the bad, and the ugly

52 min
Securing the Campaign
Security and the 2012 US Presidential Election

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

47 min
Update Computer Club
History and Not-So-Certain Future

54 min
gpg4libre - OpenPGP signing & encryption in LibreOffice
Transparently and securely use your existing keys to sign…

55 min
Because "use urandom" isn't everything: a deep dive into CSPRNGs in Operating Systems &…
Implementation, hazards and updates on use of RNGs in…

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures
61 min
Container Football
for Load Balancing and Hardware Lifecycle

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

46 min
SHOULD I STAY OR SHOULD I GO?
THE ALGORITHMIC PUBLIC SPHERE AND YOU

47 min
Working with massively distributed database systems
The CAP Theorem and Architectual Consequences
65 min
Why Germany Succeeded Where America Has Failed in Achieving Meaningful Voting Computer…
And Why All Democracies Should Follow

58 min
The Infinite Library
Storage and Access of Pornographic Information

52 min