Search for "328" returned 2060 results
59 min
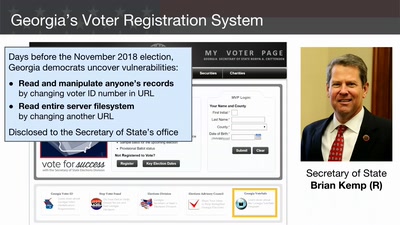
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology
53 min
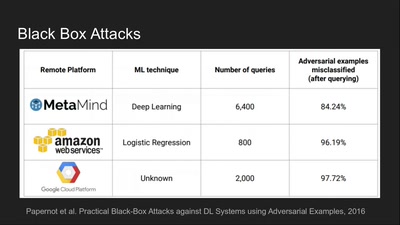
Deep Learning Blindspots
Tools for Fooling the "Black Box"

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

58 min
Switches Get Stitches
Industrial System Ownership

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
36 min
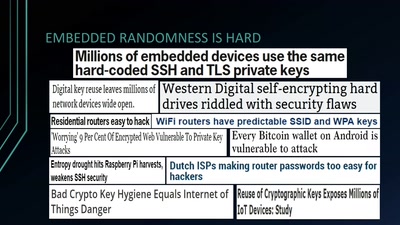
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…
31 min
Nerds in the news
Spending a year coding in a newsroom
39 min
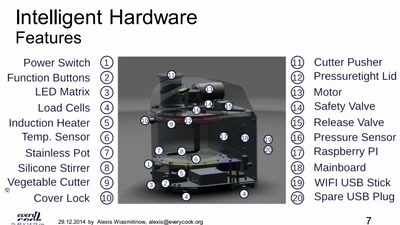
Why do we need an open food information platform
We want all data about food to be linked and public
61 min
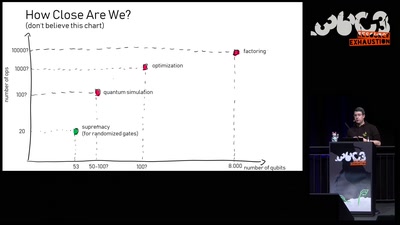
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…
64 min
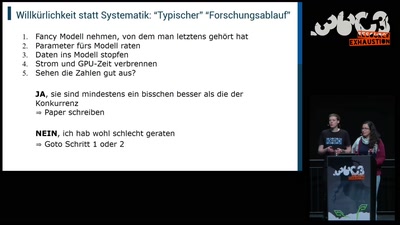
Der Deep Learning Hype
Wie lange kann es so weitergehen?

57 min