Search for "265" returned 2185 results

42 min
A world without blockchain
How (inter)national money transfers works
60 min
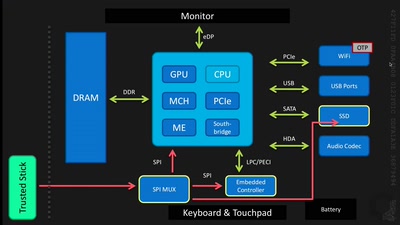
Build your own NSA
How private companies leak your personal data into the…

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

48 min
REXUS/BEXUS - Rocket and Balloon Experiments for University Students
How to bring student experiments into space.

43 min
Microtargeting und Manipulation
Von Cambridge Analytica zur EU-Wahl
41 min
Archäologische Studien im Datenmüll
Welche Daten speichert Amazon über uns?

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

30 min
apertus° AXIOM
The first Open Source Cinema Camera

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
46 min