Search for "id4=WH0n" returned 328 results

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers
38 min
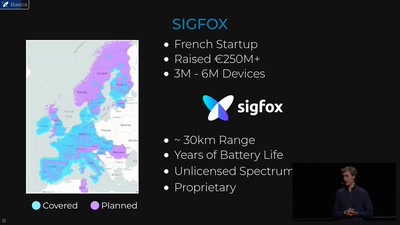
Hunting the Sigfox: Wireless IoT Network Security
Dissecting the radio protocol of Sigfox, the global…

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything
58 min
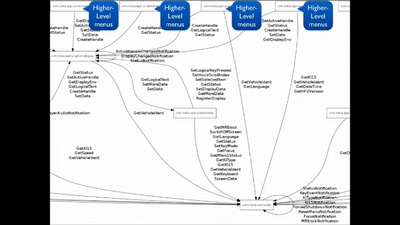
Script Your Car!
Using existing hardware platforms to integrate python into…

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology
41 min
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology
44 min
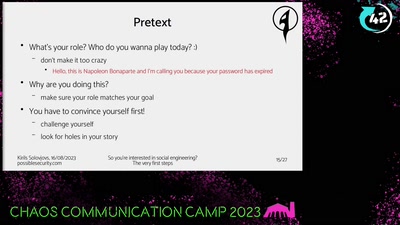
So you're interested in social engineering?
The very first steps

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
39 min
Gamified Control?
China's Social Credit Systems

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

42 min