Search for "Victor van der Veen" returned 181 results

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity
60 min
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy
41 min
SCADA StrangeLove 2
We already know
66 min
31C3 Keynote
A New Dawn

30 min
Syrian Archive
Preserving documentation of human rights violations

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…
27 min
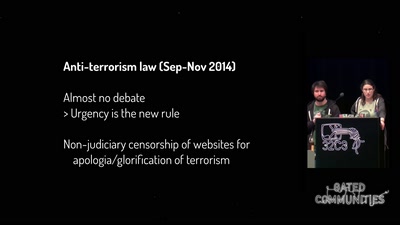
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency
31 min
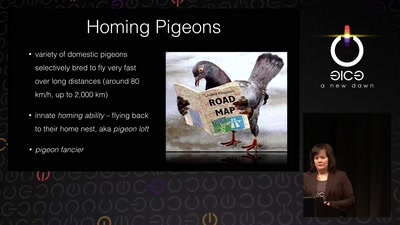
Living Drones
From war pigeons in 1914 to cyborg moths in 2014

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state
45 min
A geometry engine from first principles
the first three years of a six month project.

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption
61 min
How to Hack Your Way to Space
Bringing the Hacker Mindset to the Space Ecosphere - The…

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…
46 min