Search for "366" returned 1946 results

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Concepts for global TSCM
getting out of surveillance state mode

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

58 min
Baseband Exploitation in 2013
Hexagon challenges

55 min
White-Box Cryptography
Survey

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14
59 min
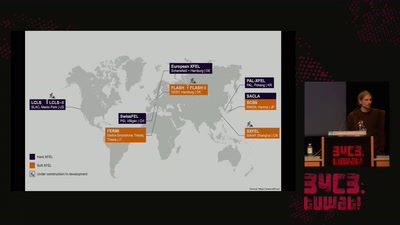
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

32 min
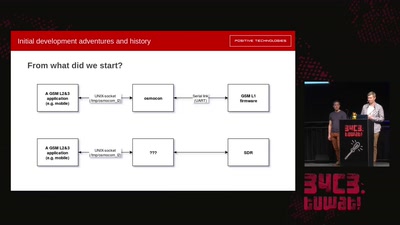
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
31 min