Search for "582" returned 1912 results

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

60 min
Best of Informationsfreiheit
Transparenz mit der Brechstange

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

69 min
Telescope Making
How to make your own telescope

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet

62 min
Kyber and Post-Quantum Crypto
How does it work?

58 min
Virtual Machine Introspection
From the Outside Looking In

58 min
When hardware must „just work“
An inside look at x86 CPU design

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

58 min
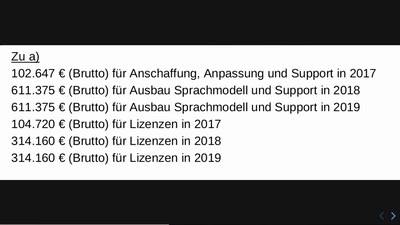
Die Krise der Bilder ist die Krise der Politik
Die Krise der Politik ist die Krise der Bilder
59 min