Search for "356" returned 2033 results

32 min
History and implications of DRM
From tractors to Web standards
31 min
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

53 min
Surveilling the surveillers
About military RF communication surveillance and other…
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

39 min
Hacking the Czech Parliament via SMS
A parliamentary drama of 223 actors
60 min
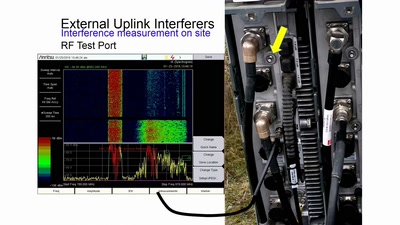
Die verborgene Seite des Mobilfunks
HF-Störquellen im Uplink

43 min
Microtargeting und Manipulation
Von Cambridge Analytica zur EU-Wahl
41 min
Archäologische Studien im Datenmüll
Welche Daten speichert Amazon über uns?

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
apertus° AXIOM
The first Open Source Cinema Camera

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation
51 min