Search for "Isa" returned 9610 results
42 min
Union Busting
What is it and why you should care

36 min
PolyCoin - A game played across MCH
How it works and what is inside it
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone

45 min
Homegrown Interactive Tables
Any Technology Sufficiently Advanced is Indistinguishable…
60 min
Data Retention in the EU five years after the Directive
Why the time is now to get active
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle
40 min
A modern manifest of cyberspace
The internet is dead, long live the internet

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
53 min
CCC Office, die neue Software
Was ist der Stand, was kann die neue Software und was wird…
17 min
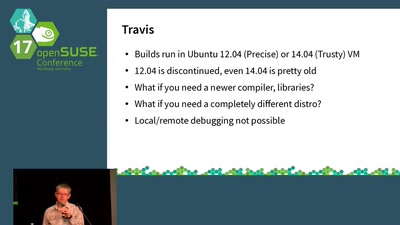
Continuous Integration using Travis and Docker
There is no excuse for NOT using continuous integration

44 min
Why technology sucks
If technology is the solution, politicians are the problem
36 min
Live: Firebird: the high performance database that you didnt know was already on your…
Installed with Libre Office, Firebird is a vastly capable…
47 min
Test-Driven Web Development
Treating your web application like the grown-up it is

52 min
Funkerspuk
radio politics in the USA and Germany in the first half of…

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…

57 min
Secure Code
Why developing Secure Software is like playing Marble…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

58 min
Let's roll out mass encryption!
'Cause mass surveillance is there for too long already

33 min
Social cooling
How the reputation economy is turning us into conformists

57 min
Cryptowars 2.0: Lessons from the past, for the present
It's not only Hollywood who is out of ideas

54 min
Fileserver online
Fileserver ausschließlich online? Oder in Kombination mit…
38 min
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used
48 min
